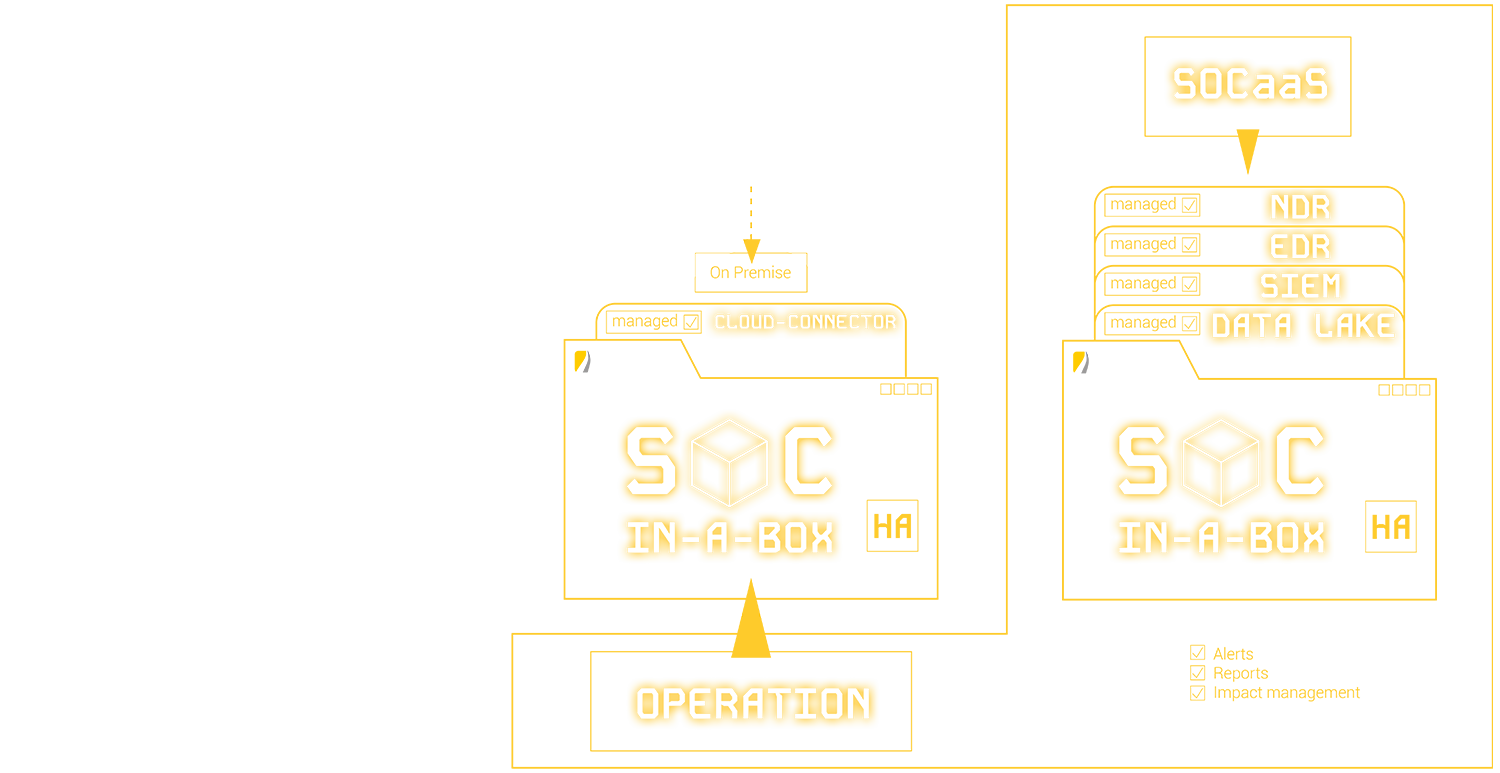
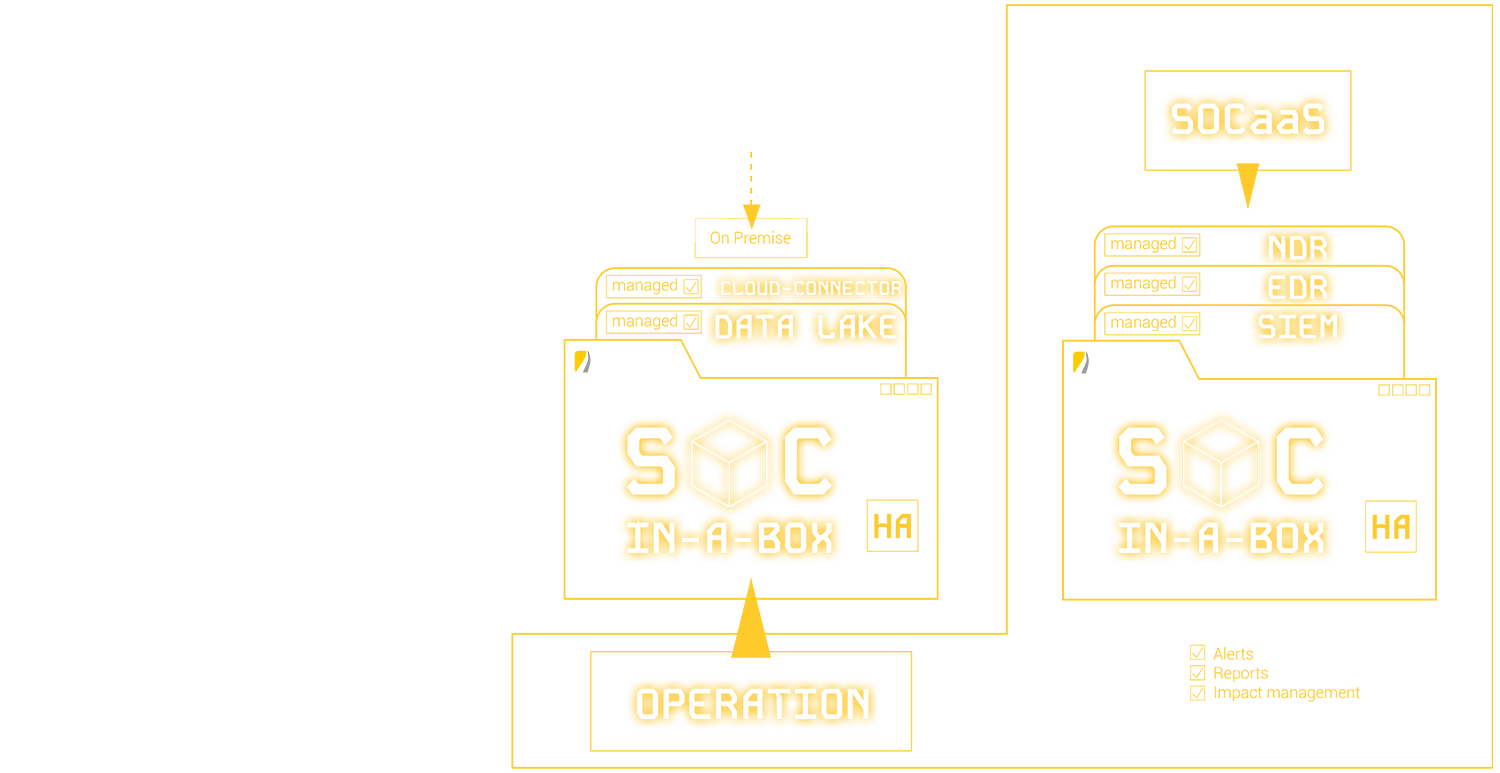
The ideal Solution for your IT Security
SOC-in-a-Box: Your modular security operations center that combines hardware, software, and service in one flexible package. Developed by our experts at doIT solutions, this complete solution offers comprehensive protection for your IT infrastructure - no matter how large or complex your requirements are.
Modular & Scalable
SOC-in-a-Box impresses with its unique modular design, which allows you to combine almost all services. Whether you choose the Enterprise version for maximum flexibility or the all-round carefree Foundation version: you get exactly the protection your company needs. Our solution scales with your requirements and offers 24/7 incident response to detect and mitigate threats in real time.
Active Protection & Optimization
Our solution goes beyond mere monitoring. doIT's team of experts proactively responds to detected anomalies and offers customized optimizations and settings that continuously improve your IT security. Whether it's suspicious activity on endpoints, running services, or in-data traffic – SOC-in-a-Box ensures that you are protected at all times.
Continuous Security Consultation
Our service includes regular security workshops by security consultants to train your employees and continuously optimize your security strategy. In this way, we guarantee constant development of corporate security and ensure that you are always one step ahead of current threats.
Cybersecurity-as-a-Service (CSaaS)
Our CSaaS offers you comprehensive protection directly on site, including 24/7 incident response and continuous development through regular workshops. Thanks to alert engineering, we optimize your security alerts to prevent "alert fatigue". Scalable according to log volume, our SOC-in-a-Box stores your data securely for at least 365 days and gives you full access to your data at any time.
Benefit from doIT's Cyber Security Experts' Know-how
Still at the beginning or concrete ideas already? We are here to help you!
If you have already found a specific topic in the area of cyber security, feel free to arrange an IT security deep dive with us, where we can go into more detail together. If you don't yet have a concrete idea of how to set up your IT security, we are also happy to give you some advice. Arrange your appointment now and protect your company from cyber attacks!
Compliance made easy
With our SOC-in-a-Box, fulfilling compliance regulations will become hassle-free. We'll help you to effortlessly meet all regulatory requirements and keep your IT infrastructure audit-ready at all times. Trust in our expertise to minimize your compliance risks.
Secure OT Infrastructure
We offer comprehensive concepts in order to detect attackers in your OT infrastructure at an early stage and locate them precisely - whether on switching systems, in the cloud or directly on operational devices. Our security solutions ensure the protection of all critical components that modern companies rely on today.
SOC as a Service
| General | |
|---|---|
| SOC Service made in Germany | YES |
| Support for On-Prem SOC deployment | YES |
| Support for Cloud-based SOC deployment | YES |
| Use Cases for IT and OT Infrastructure | YES |
| SOC as a Service for custumer owned tools (BYO) | YES |
| Security Consulting workshops (2/year) | YES |
| Additional Consulting workshops | optional |
| Standard Reporting | YES |
| Custom Reporting | optional |
SOC as a Service
| Response | |
|---|---|
| Alerting via Service Portal & E-Mail & SMS | YES |
| Custom Ticket System integration | optional |
| Active Remedication | YES |
| Standard Response Workflows | YES |
| Custom Response Workflows | optional |
| 10/5 standard SLA (SLA L1: 30min / L2: 4h / L3: 4h) | YES |
| 10/5 extended SLA I (SLA L1: 30min / L2: 1h / L3: 2h) | optional |
| 10/5 extended SLA II (SLA L1: 15min / L2: 30min / L3: 1h) | optional |
| 24/7 standard SLA: Level 1 Response (SLA L1: 30min) | YES |
| 24/7 standard SLA I: Level 2 + 3 Response (10/5 SLA + 30min; critical incidents only) | optional |
| 24/7 standard SLA II: Level 2 + 3 Response (10/5 SLA + 15min) | optional |
SOC as a Service
| Service Addons | |
|---|---|
| Indicator Enrichment | YES |
| Threat Intelligence Service | optional |
| Threat Intelligence Service additional Darkweb Monitoring | optional |
| Vulnerability Management Service | optional |
| Threat Hunting Service | optional |
| Deception Service + Honeypots | optional |
| Incident Response Retainer | optional |
| Customer Success Manager | optional |
| Security Awareness Service | optional |
| Attack Surface Management Service | optional |
| Audit Access to doIT Case Management System | optional |
Technology EDR
| Cloud | On-Prem | |
|---|---|---|
| Min Capacity (Endpoints) | 200 | 500 |
| High Availability | YES | YES |
| Agent Monitoring | YES | YES |
| Technology Access | YES | YES |
| Default Data Retention | 31 | 180 |
| Additional Data Retention | optional | optional |