Detect, Respond, Improve
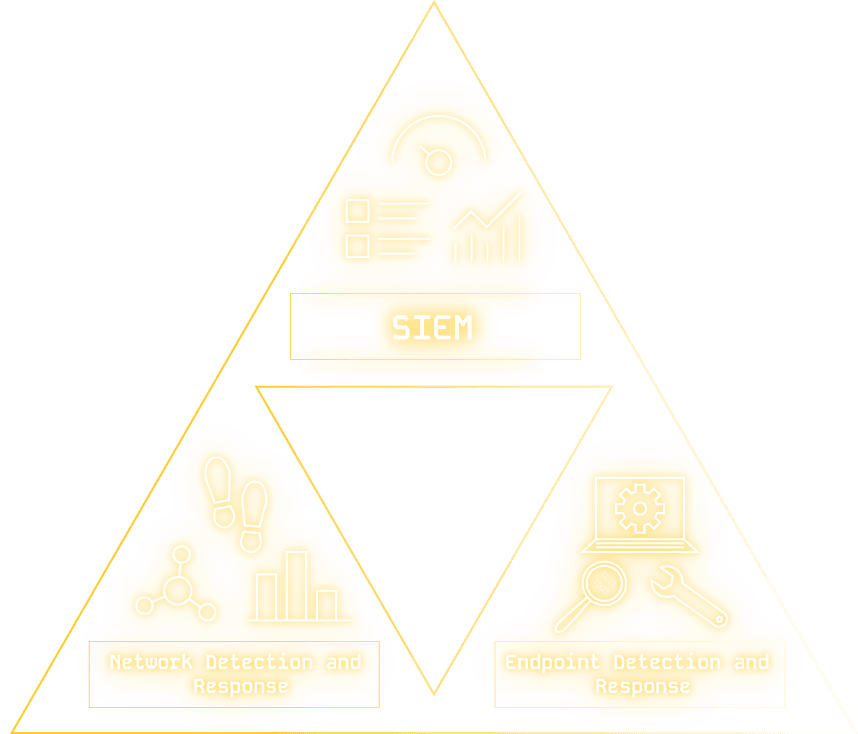
A technology without a process behind it is not very functional. When an attack is underway, it is important to detect it as early as possible. This is the only way to react to incidents quickly and prevent worse from happening. The aim here is not to build the largest possible IT security solution, but to focus on the important points. A good approach is the implementation of the SOC Visibility Triad.
Yet attack detection is not enough. Every detection must trigger a comprehensible reaction and, if necessary, escalation. This process must be subject to continuous optimization in order to ensure long-term efficiency and effectiveness.
We evaluate these events and optimize both the configuration of your detection modules and the subsequent reaction. This means that your IT security develops in line with the requirements of your company.
Our Service
Our CI service focuses on effectively detecting attacks so they can be repelled as quickly as possible. The automated processes and the implementation of our SOAR (Security Orchestration, Automation and Response) enable an efficient response to attacks.
The SOC Visibility Triad refers to three fundamental elements that are essential for effective monitoring of IT systems. These elements include:
- Endpoints: An EDR solution provides companies with a proactive approach, protecting their endpoints and data by detecting threats early and preventing them from causing damage.
- Event monitoring: By using SIEM, companies can also create and apply event monitoring policies and rules to ensure that security protocols are followed.
- Network: An NDR solution provides an additional layer of protection at the network level by monitoring all network traffic to detect anomalies and suspicious activity.
Overall, the SOC Visibility Triad is an important part of a comprehensive IT security approach as it helps companies detect threats early, respond quickly, and minimize potential damage.
Well prepared for the Future!
Only 50% of successful security monitoring consists of functioning and professionally operated technology. The other half is a well-maintained organization that is able to select the appropriate monitoring measures and implement them technically, as well as strive to ensure quality on a permanent basis. In addition, clear processes must be defined in order to respond quickly and efficiently in an emergency. In order to support you in this challenge, our Cyber Intelligence Service closes the gap between operational IT, IT security and IT risk/security management.
We'll take care of it - everything else is mere details.