Monitoring Devices, Isolating Malware
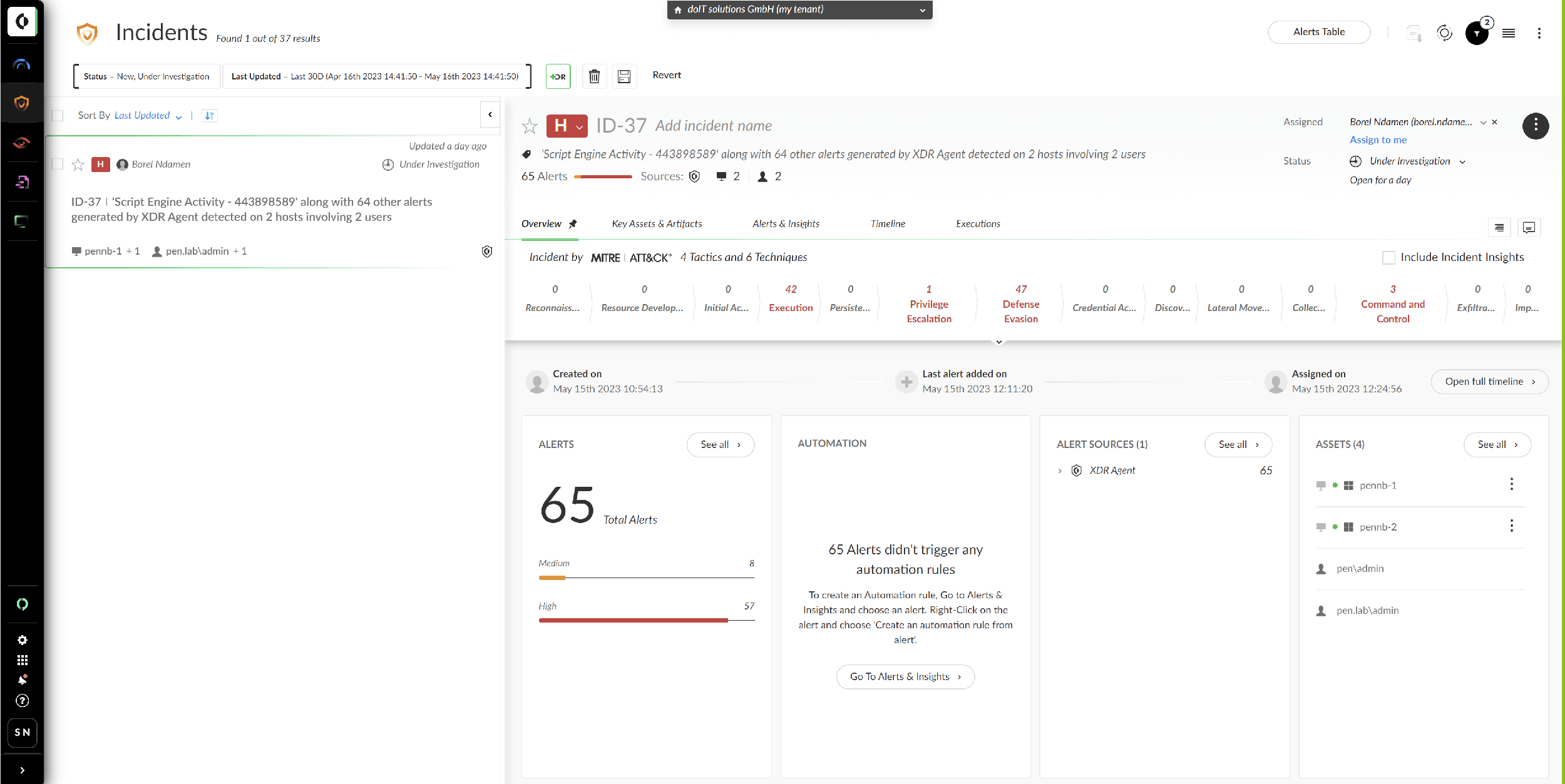
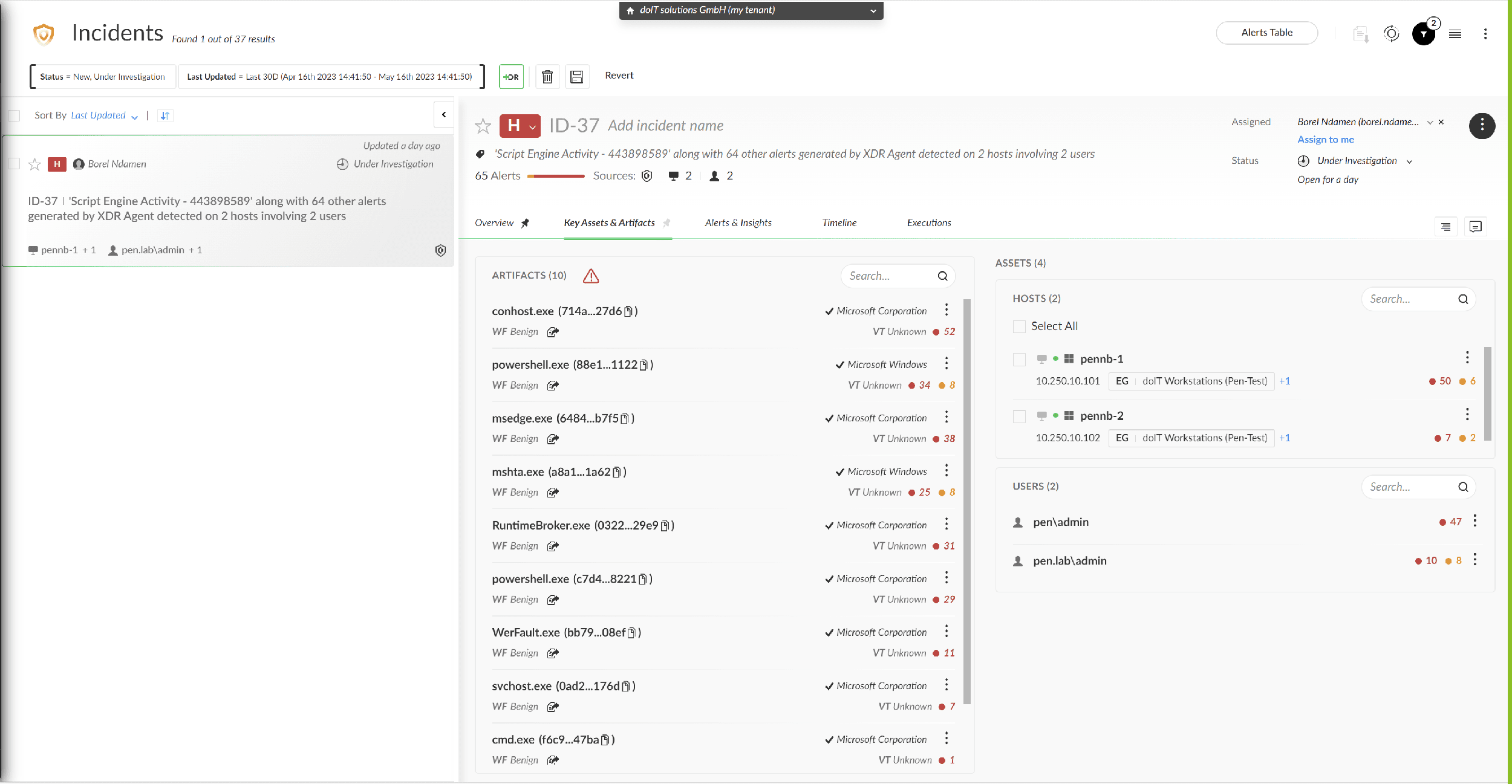
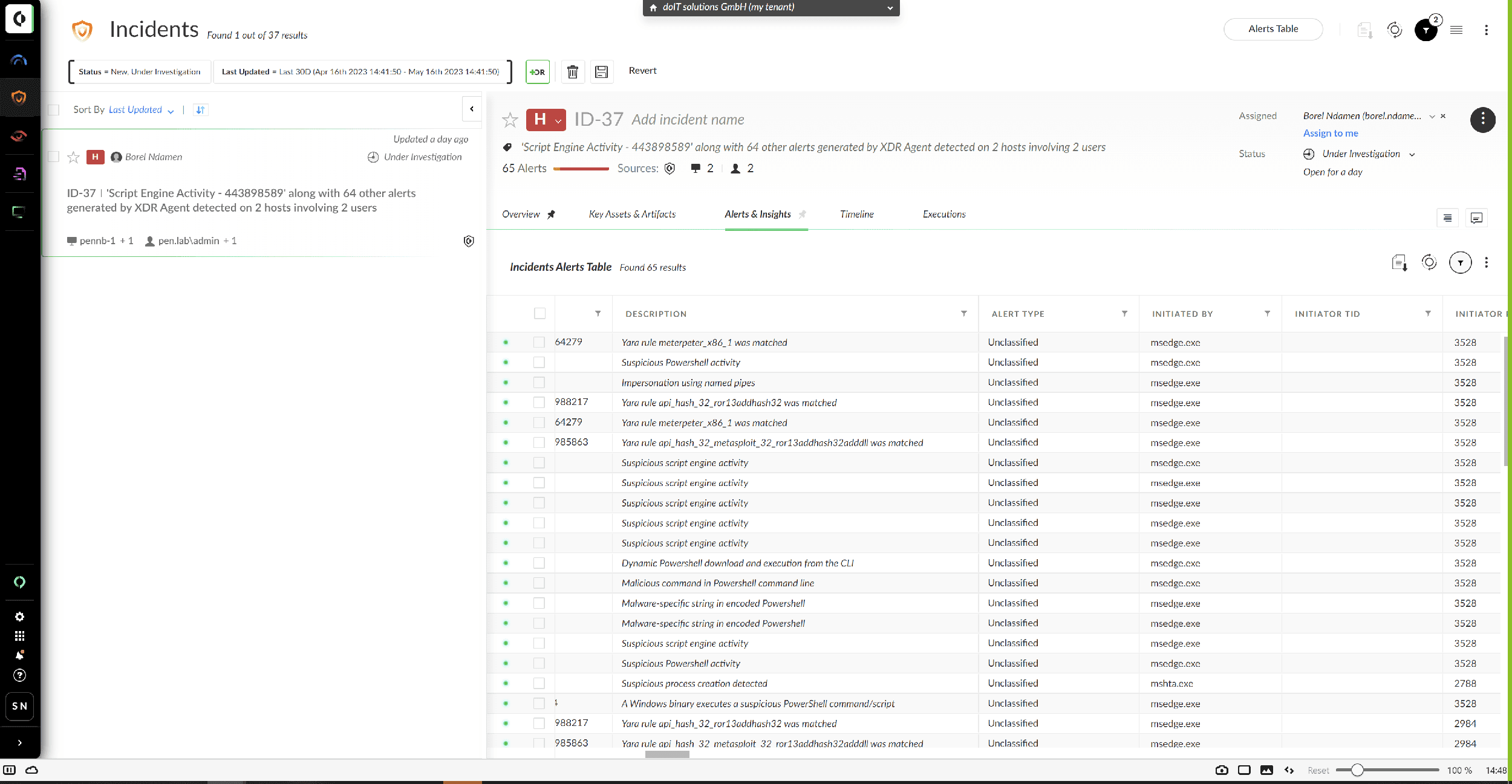
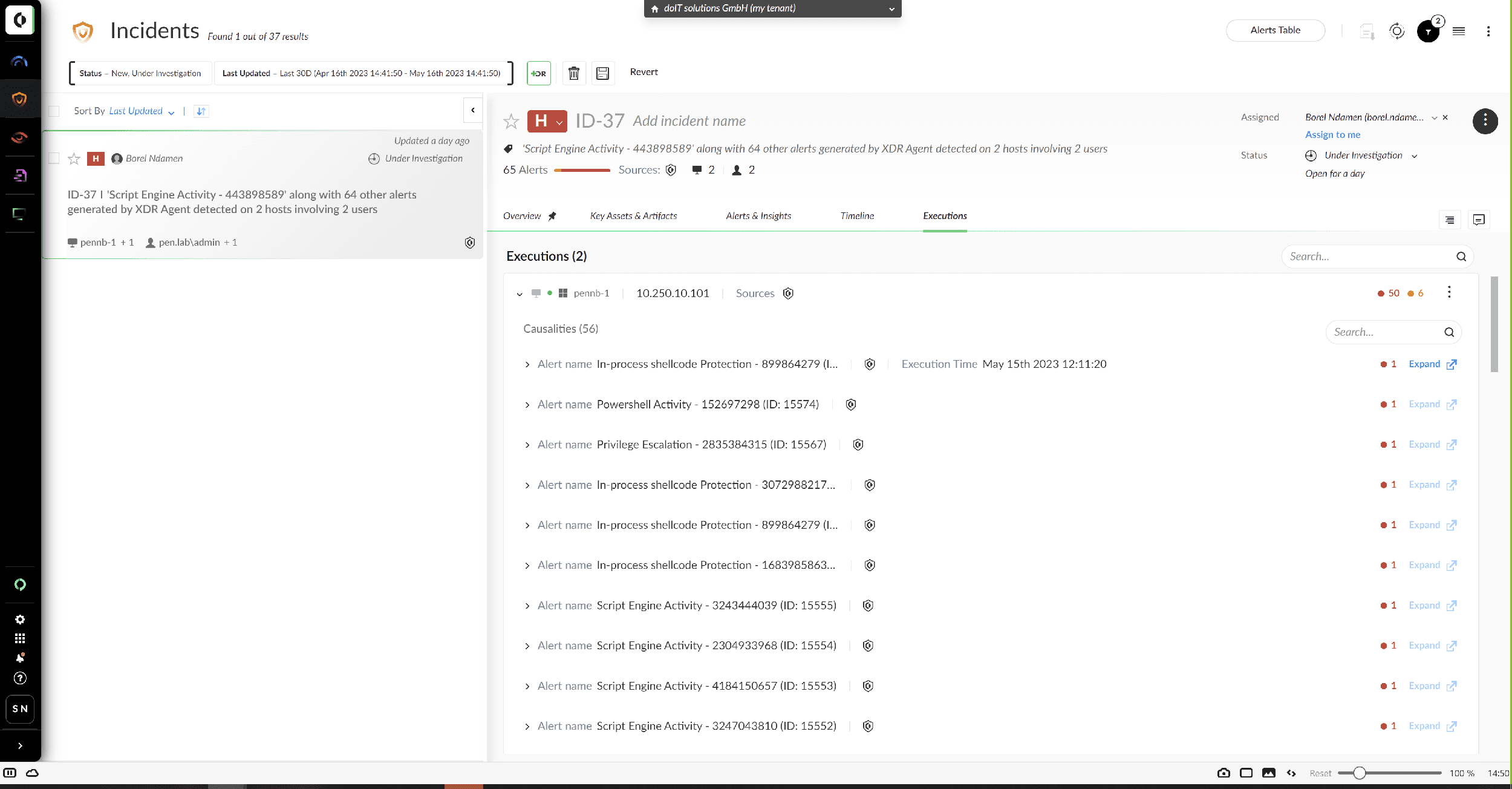
This module is used to precisely and safely identify and isolate machines in the network infected with malware. Even unknown malicious code is recognized and blocked based on its behavior. This module monitors all endpoints, such as company laptops, for potentially suspicious behavior. Detailed information about applications and processes on the devices can also be accessed here. This includes file access, network connections or the launch of child processes for each process started on the endpoint.
In an emergency, this will help you assess the potential damage and take targeted countermeasures.
The optional extension NGAV (Next-Generation Antivirus) uses the most modern standards for virus detection and control and thus offers maximum combined protection for your IT landscape.
Why do we use Palo Alto Cortex for EDR
We chose Cortex because we believe it offers the best technical combination of attack detection, data analysis and configurability. Palo Alto is known as a best-of-breed manufacturer and, if required, also offers a comprehensive security concept through its platform strategy and AI-based approaches.
Cortex offers comprehensive coverage of MITRE ATT&CK and provides excellent results and outstanding performance. In addition, it has important business functions such as single sign-on and SAML authentication, which increase user convenience and security. Cortex is also available in both single and multi-tenant versions, which allows flexible adaptation to operational requirements.
Thanks to Cortex, you have all the information you need to quickly react and ensure the security of your IT system. With this solution, you are able to detect and ward off potential threats before they can cause damage. This means you can effectively protect your business processes and confidential data at all times.
Why do we use elastic for EDR?
Elastic Defend is the ideal choice for state-of-the-art endpoint detection and response (EDR). The solution combines real-time threat detection and powerful data analysis to ensure comprehensive protection. Thanks to machine learning and automated threat prevention, attacks can be identified and contained at an early stage.
Elastic also offers a scalable, customizable platform that grows with the needs of thriving companies. What's particularly attractive is that Elastic Security can be easily integrated into existing systems, offers a central security overview and thus reduces complexity and response times. The result is future-proof, cost-effective protection that is always ready to maximize your security.
What is the strength of our EDR in terms of detecting threats?
An EDR system provides proactive monitoring of endpoints to quickly detect and respond to threats. It provides detailed information about all technical operations on the endpoint that can only be made visible using this technology. It can detect unusual activity or behavior by users or devices that may indicate an attack. If an attack is detected, the EDR system can quickly take local action to stop the attack and prevent the spread of malware.
In addition, an EDR system provides central monitoring and control of endpoints, enabling effective management of patches, updates and security policies. This helps to minimize vulnerabilities and increase protection against attacks.
Benefit from doIT's Cyber Security Experts' Know-how
Still at the beginning or concrete ideas already? We are here to help you!
If you have already found a specific topic in the area of cyber security, feel free to arrange an IT security deep dive with us, where we can go into more detail together. If you don't yet have a concrete idea of how to set up your IT security, we are also happy to give you some advice. Arrange your appointment now and protect your company from cyber attacks!