The central Hub for your IT Security
This is where all security-relevant information and reports about connected systems are brought together. SIEM stands for Security Information and Event Management and forms the backbone of your SOC. If there is a fire somewhere, you will see it here. The SIEM compares its data with previously documented attack patterns and raises an alarm if necessary. At the same time, you still have access to historical data for analysis purposes.
Why we rely on Splunk Enterprise Security
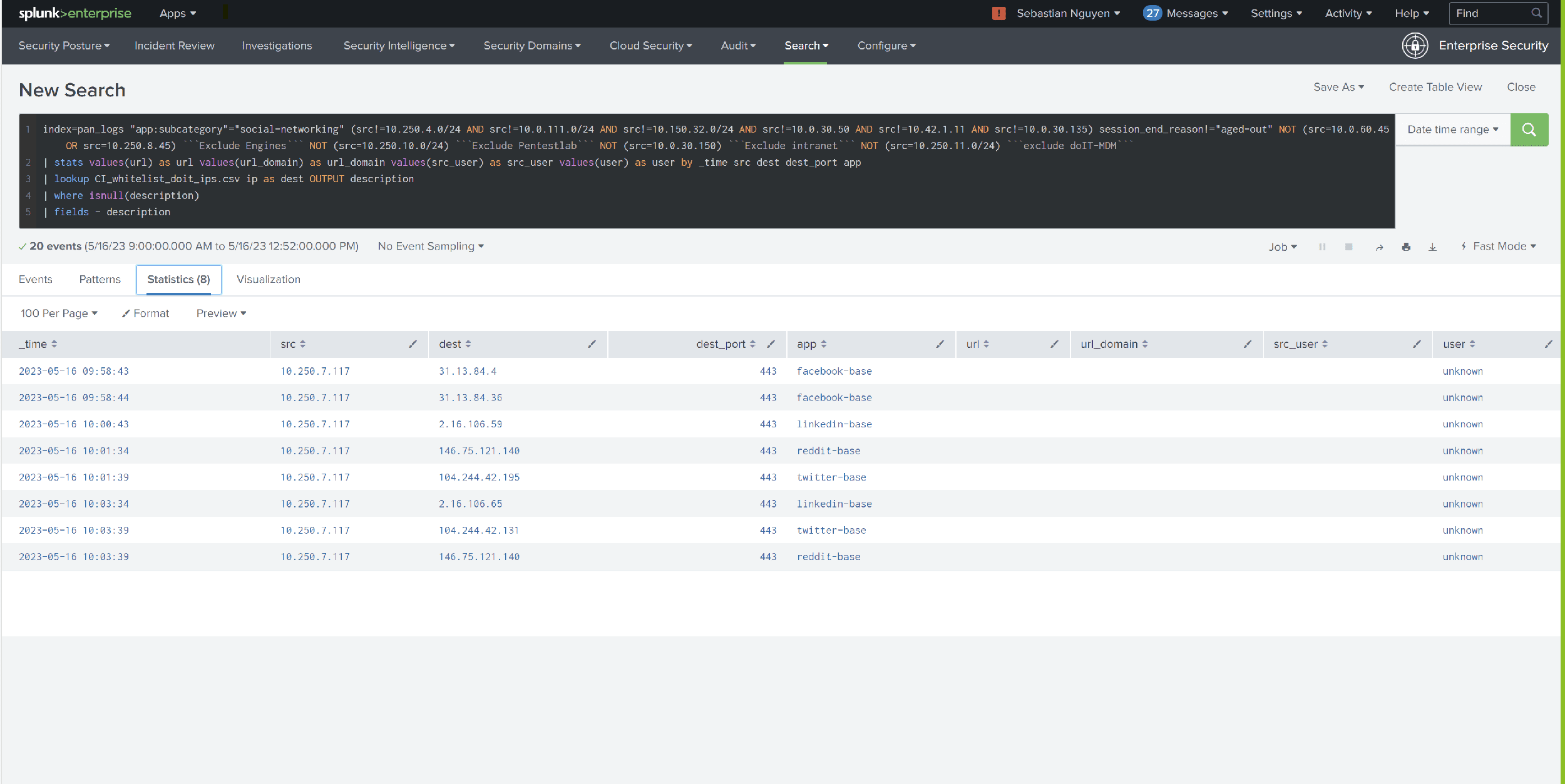
A well-functioning Security Information and Event Management (SIEM) system is essential for a successful IT security strategy. It is important that the system is able to handle the most diverse data structures generated by different applications. This is where Splunk comes into play, as it can easily put unstructured data into context with all other logs. Splunk is therefore the ideal option for processing a wide variety of log types and achieving very good results.
Why we rely on elastic
With elastic it is possible to cost-effectively expand existing or new SIEM installations.
Depending on the data source, elastic is the best possible analysis platform.
For basic requirements, the use of the open source variant enables an inexpensive start into the world of log data processing.
Why we use Cribl Stream
Cribl Stream complements the SIEM system with powerful data routing and transformation. The complexity of data processing has increased in recent years due to hybrid and cloud-native developments in IT.
In order to be able to map all current and future requirements in the best possible way, we use Cribl Stream as a central data router.
Cribl Stream complements the SIEM system with powerful data routing and transformation. The complexity of data processing has increased in recent years due to hybrid and cloud-native developments in IT. In order to be able to map all current and future requirements in the best possible way, we use Cribl Stream as a central data router. The exceptional scalability and flexible options for routing data ensure that the most suitable target system is always fed with the right data. Easy-to-manage transformation and filter rules allow these to be preconditioned optimally and in a space-saving manner.
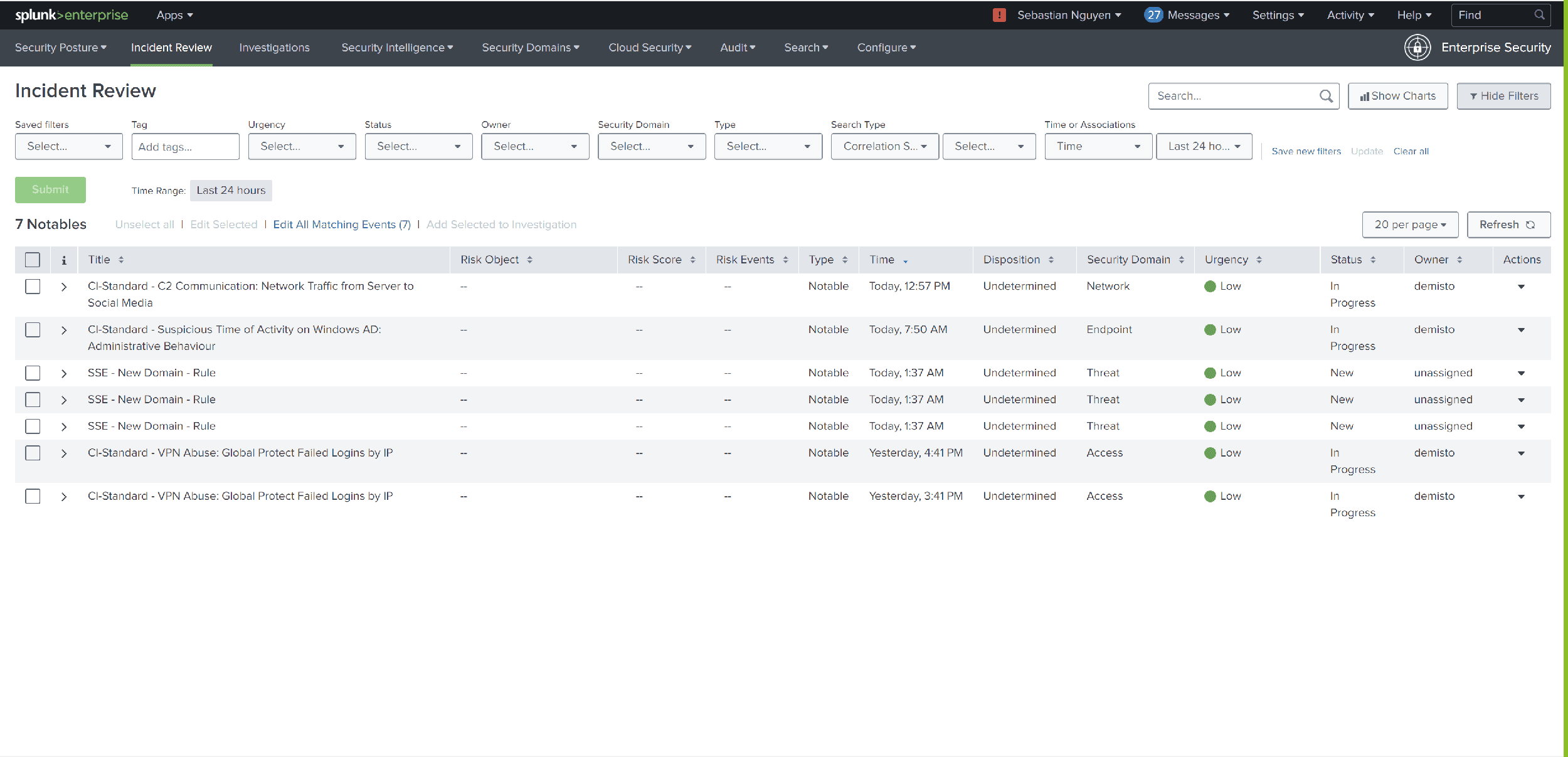
What is the Strength of SIEM in Attack Detection?
Many systems can be protected with Network Detection and Response (NDR) or Endpoint Detection and Response (EDR), but there are also applications that cannot be secured with such measures.
In such cases, SIEM comes into play. SIEM is able to collect, correlate and evaluate data from a wide variety of systems and applications in order to identify potential security threats. A classic SIEM use case is monitoring user permissions in applications. For example, if a new user is created and suddenly receives admin rights, this can be an indication of a possible threat.
A SIEM system can detect such changes in user access in real time and issue the necessary alerts in order to be able to respond quickly to potential security threats. SIEM is therefore an important part of any comprehensive IT security strategy and offers companies the opportunity to monitor and protect their systems and applications around the clock.
Benefit from doIT's Cyber Security Experts' Know-how
Still at the beginning or concrete ideas already? We are here to help you!
If you have already found a specific topic in the area of cyber security, feel free to arrange an IT security deep dive with us, where we can go into more detail together. If you don't yet have a concrete idea of how to set up your IT security, we are also happy to give you some advice. Arrange your appointment now and protect your company from cyber attacks!