Verification of the Effectiveness of Security Measures
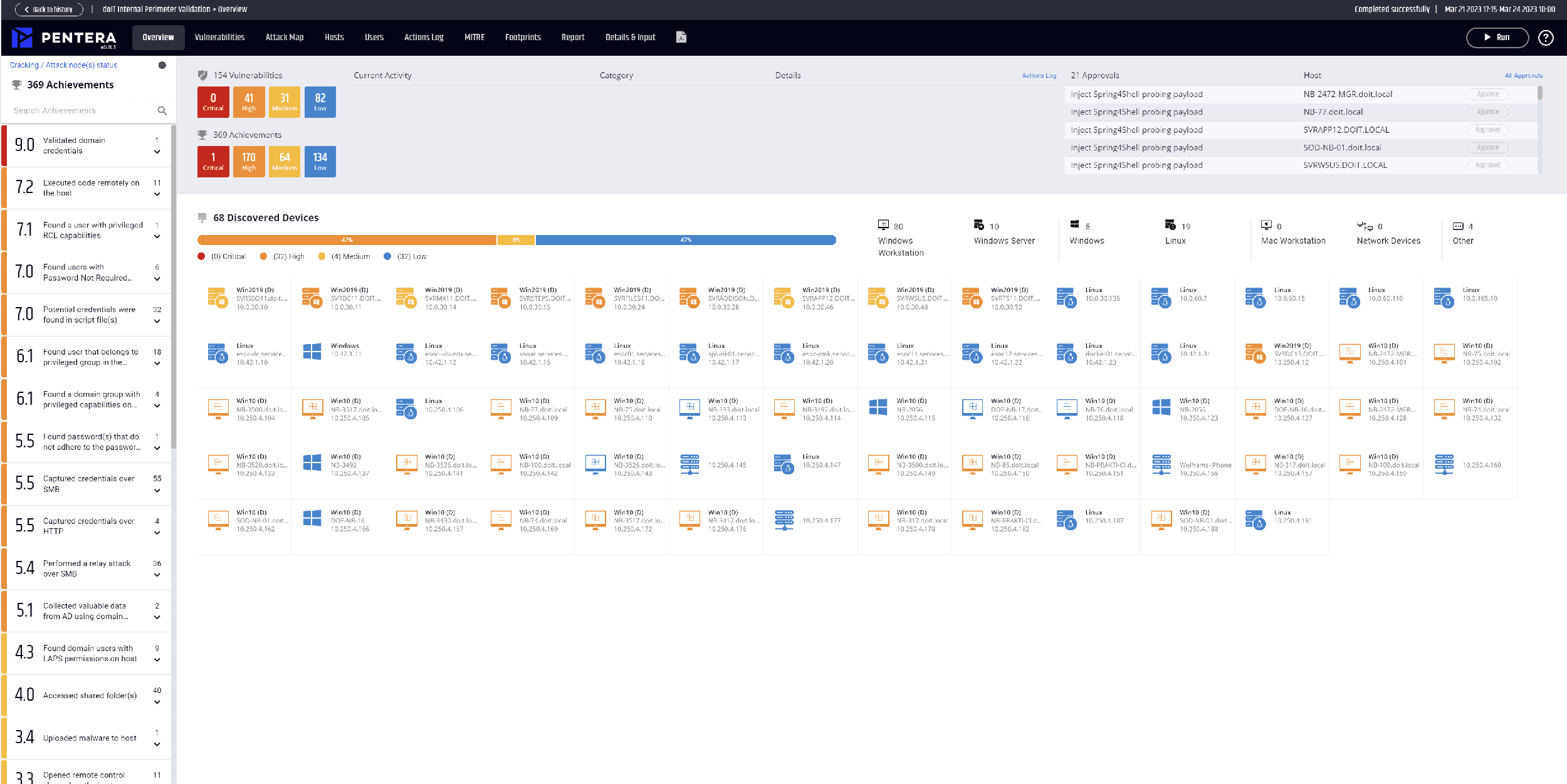
Security validation refers to the process of verifying the effectiveness of security measures and controls in an IT system or IT infrastructure. This process involves the systematic evaluation of security mechanisms and procedures to determine whether they are sufficient to detect, prevent or ward off threats and attacks.
Why do we count on Pentera for security validation?
At doIT, we trust in Pentera's innovative technology, which enables us to protect our customers continuously and comprehensively against cyber attacks.
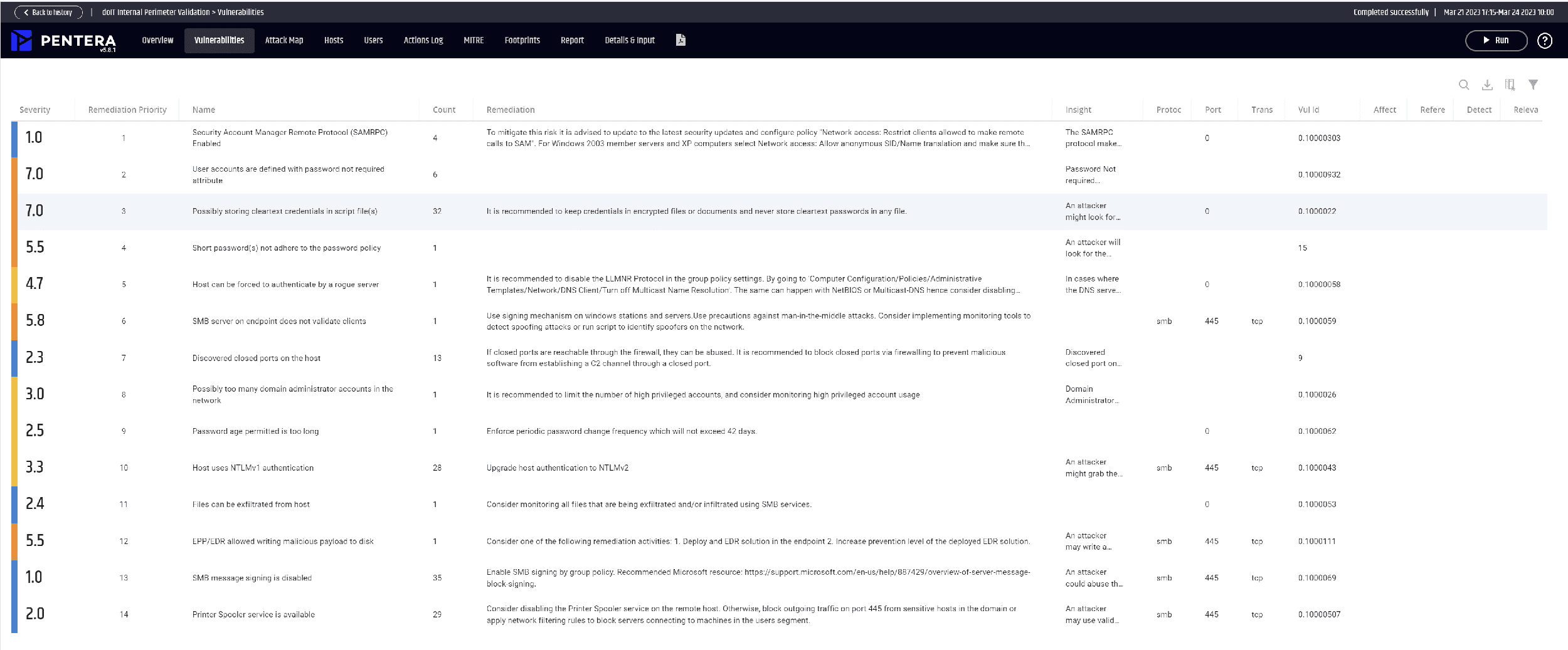
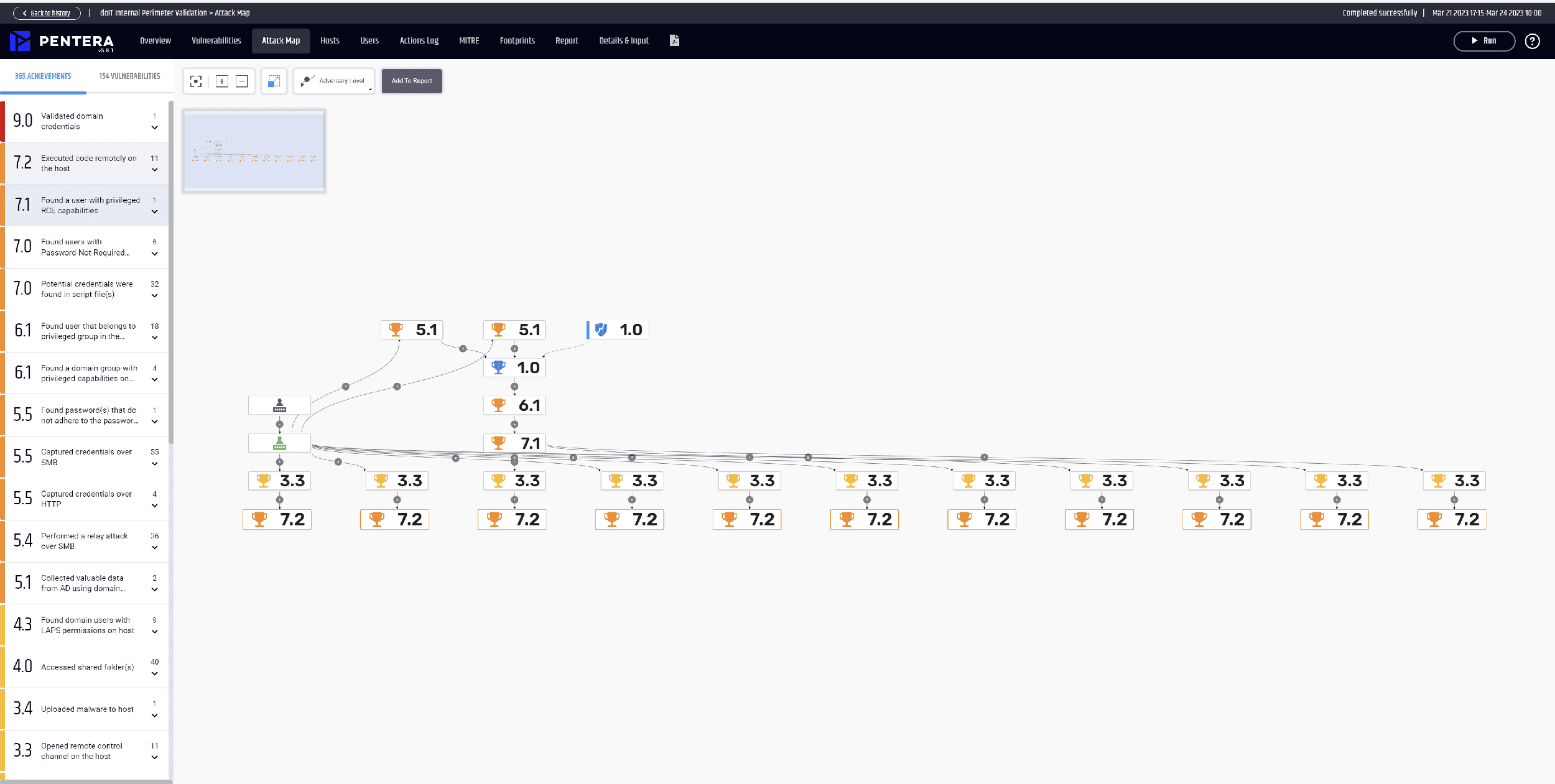
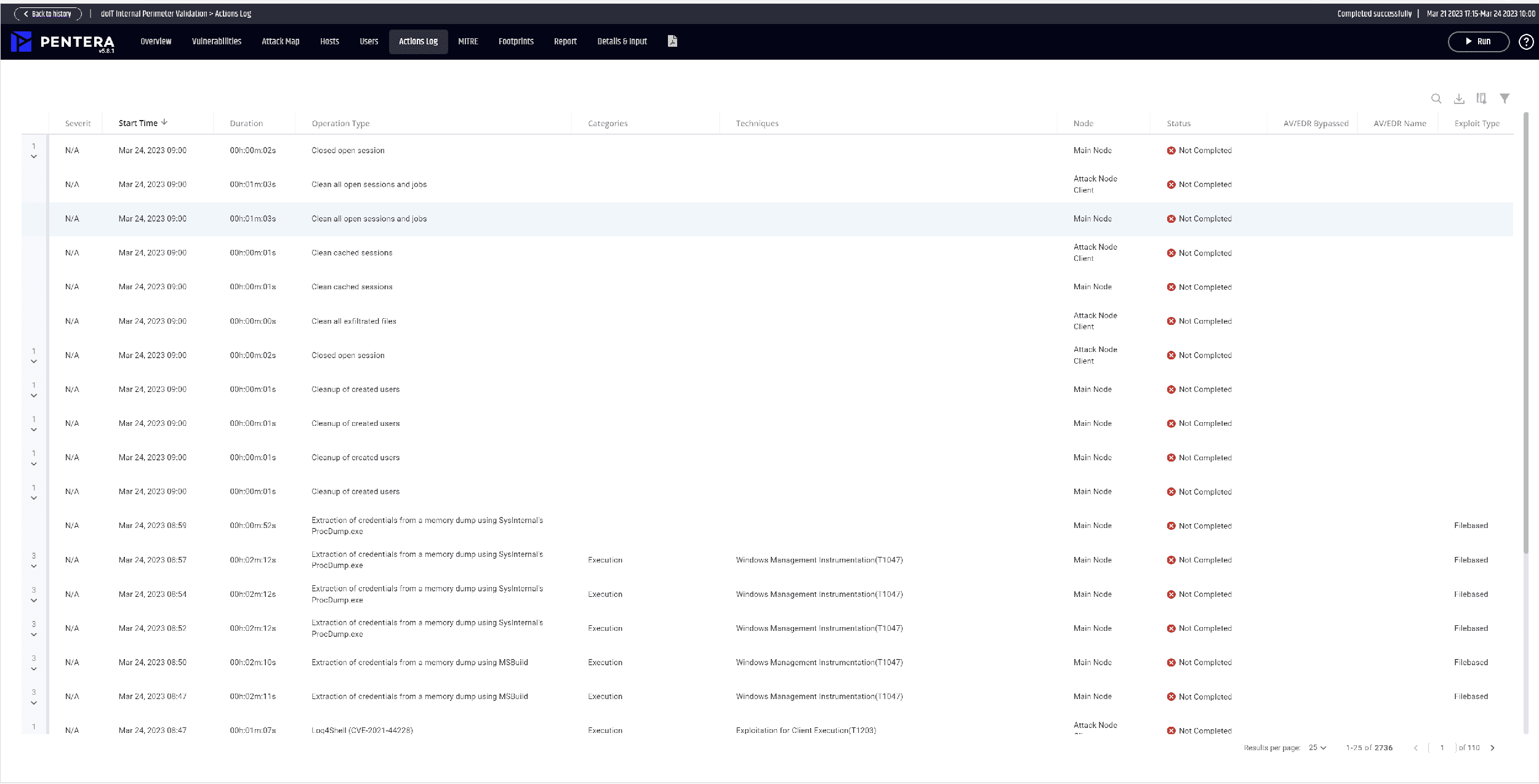
With their security validation tool, Pentera offers a unique opportunity to check all areas of IT security. Not only are theoretical vulnerabilities analyzed, but actually available exploits and hacks are also used to put the security measures to the test. You can watch our webinar to see how Security Validation with Pentera helps you focus on the real problems.
The tool simulates all attack scenarios that can be used by cyber criminals - from the use of ransomware to zero-day exploits. The tests are constantly updated and kept up to date in order to always be one step ahead of the constant developments in cybercrime.
In contrast to a conventional pentest, Pentera's security validation is continuous and automated. This makes it much more effective and comprehensive than traditional security testing and offers better protection against increasingly complex threats.
What is the Strength of Security Validation in Threat Detection?
The threat landscape in IT security is constantly changing and companies need to ensure that their security measures keep up with the latest threats.
Therefore, validating security measures is an important part of every company's IT security strategy. It is not enough to simply implement security measures and rely on them to work. Instead, their effectiveness must be tested regularly to ensure that they are able to defend against current threats.
This is where security validation comes into play. It is a method to check the effectiveness of security measures and ensure that they can detect and prevent threats. The goal of security validation is to uncover vulnerabilities and potential security holes before attackers can exploit them.
Benefit from doIT's Cyber Security Experts' Know-how
Still at the beginning or concrete ideas already? We are here to help you!
If you have already found a specific topic in the area of cyber security, feel free to arrange an IT security deep dive with us, where we can go into more detail together. If you don't yet have a concrete idea of how to set up your IT security, we are also happy to give you some advice. Arrange your appointment now and protect your company from cyber attacks!