Helpful Insights
Especially in today's hybrid environments, it is becoming increasingly difficult to inventory all assets and keep them up to date. This makes targeted asset management for all end user devices with access to the infrastructure all the more important. Detailed knowledge of existing assets and identities is the foundation for efficient incident processing.
Why do we rely on Axonius for Security Asset Management?
Thanks to its comprehensive functionality, integrations, automation and customization, Axonius Security Asset Management is a powerful solution to effectively manage your IT assets and identities, identify vulnerabilities and improve the security of your corporate environment. It enables companies to achieve a complete and accurate inventory of their IT assets and identities, manage them centrally and serve as a source of information for other systems.
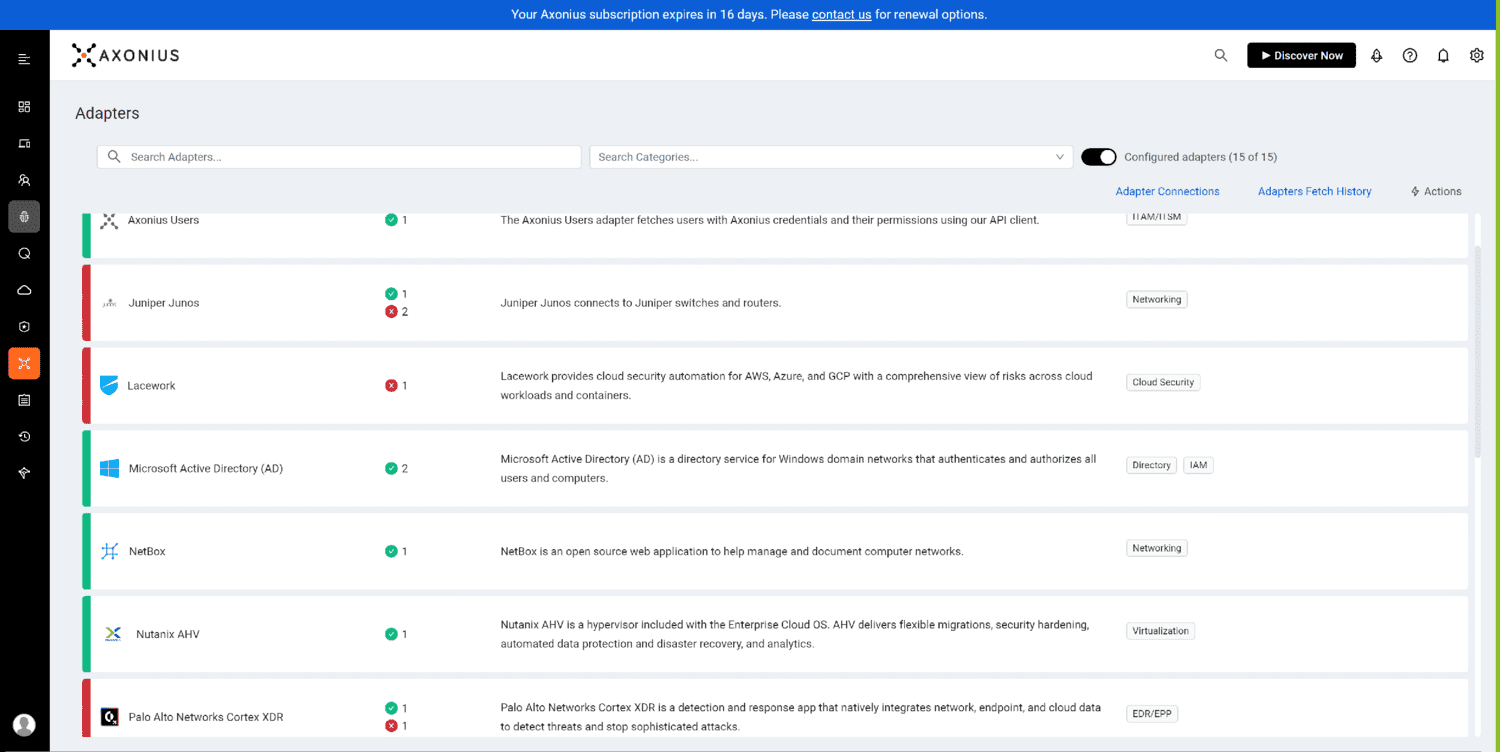
What makes Axonius special is its ability to seamlessly integrate and consolidate a variety of data sources and security tools. It can communicate with a variety of systems and platforms, including endpoint security solutions, cloud services, network devices and more. This gives you a holistic view of your IT infrastructure and allows you to identify potential security gaps. The extensive framework offered by the manufacturer reduces the integration effort immensely.
In addition, Axonius offers advanced automation features that reduce time-consuming manual processes. It can automatically collect asset data, perform consistency checks, detect vulnerabilities and monitor compliance requirements. This not only saves you time and resources, but also improves the efficiency and accuracy of your security measures.
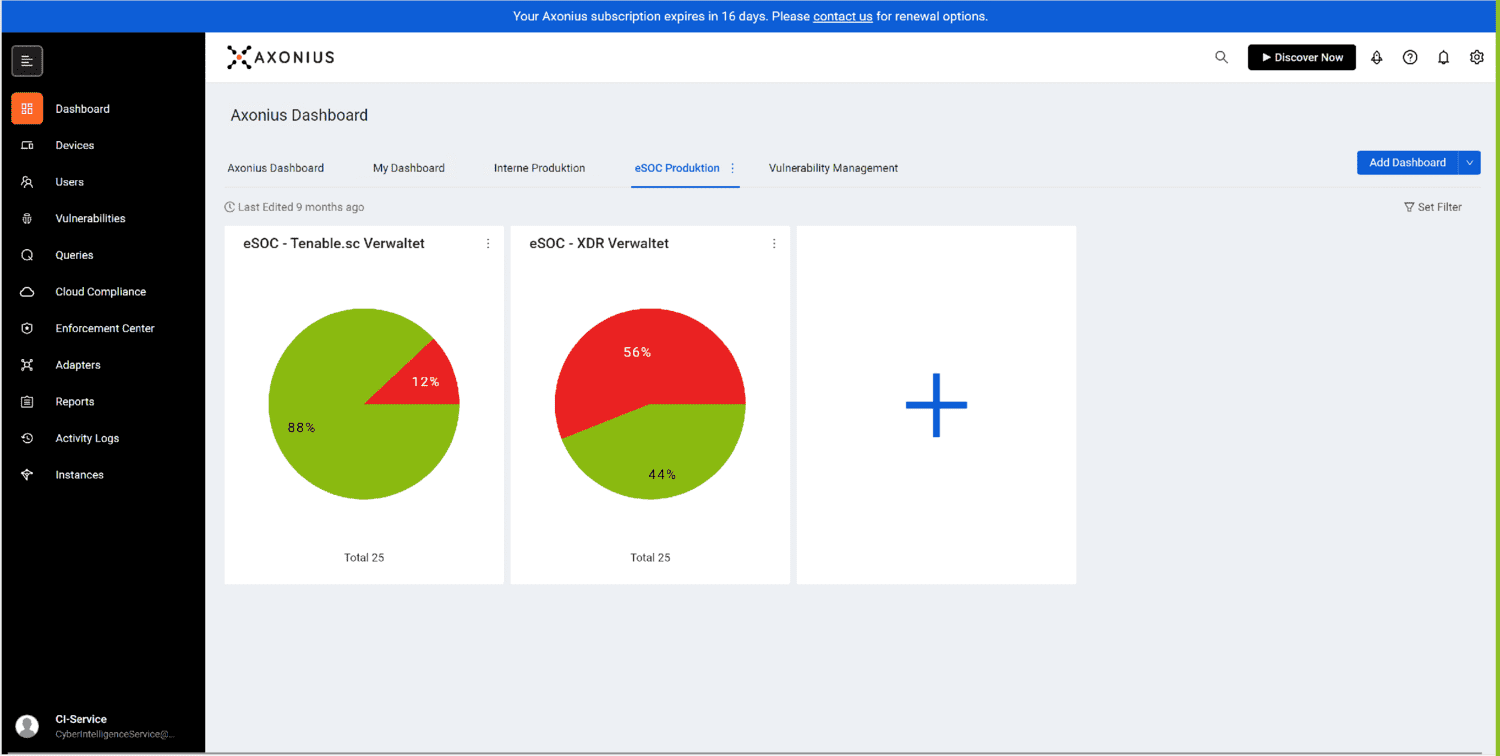
Another important aspect of Axonius is its flexibility and customizability. It allows you to set individual policies and rules to meet specific security requirements of your company. It can also create custom reports and dashboards to give you a clear and meaningful overview of the health of your assets and their security posture.
What is the Strength of Security Asset Management in accelerating IT Security Processes?
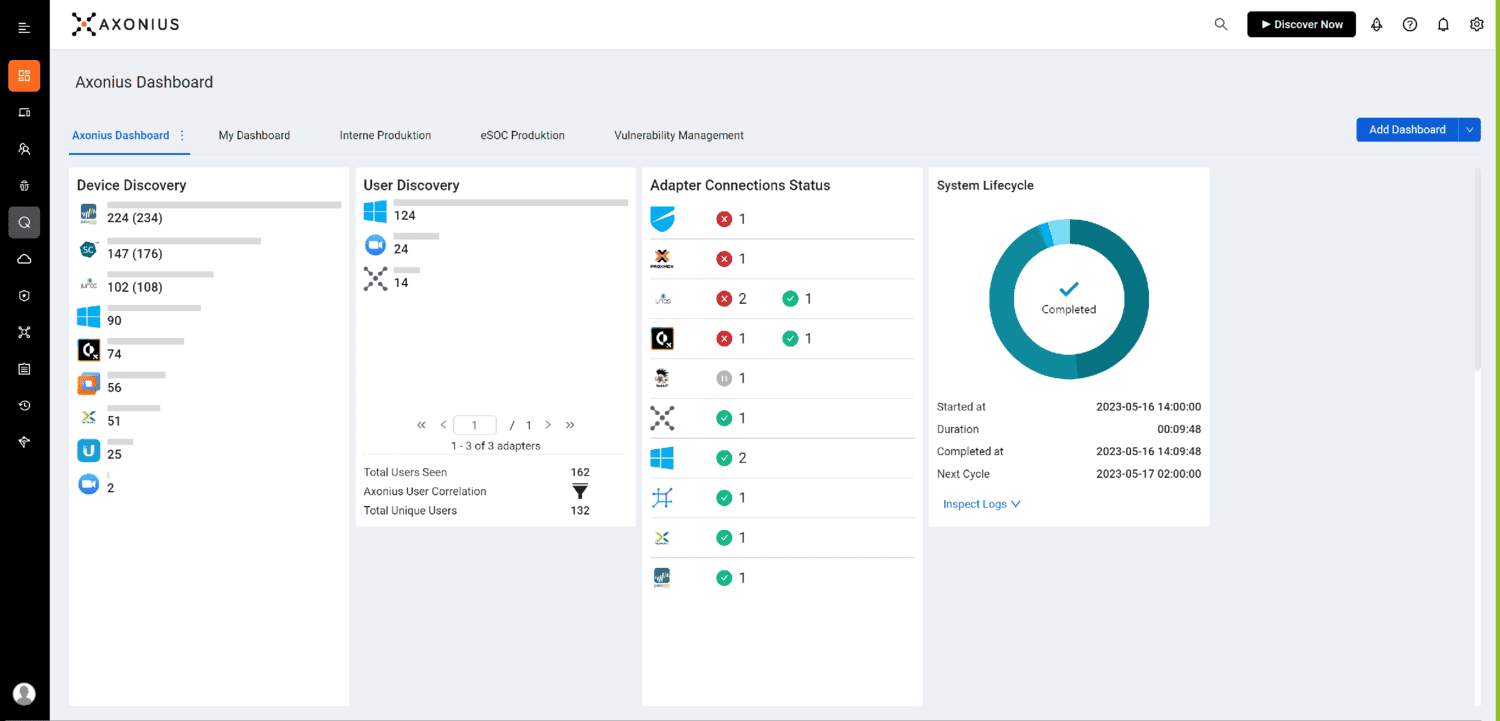
Asset Management is crucial for a company's IT security. It enables a real-time view of the connected devices and creates a comprehensive overview of the infrastructure. Instead of laboriously maintaining lists, our Security Asset Management collects all available information from every device and presents it clearly. This provides information such as server location, network activitie, user access and a list of the assets present. speeding up as well as simplifying processes.
Of course, you could search for this information manually, but with our Security Asset Management it is easy, quick and convenient. It saves valuable time and resources, while at the same time increasing the efficiency and effectiveness of security incident investigations. It enables an efficient response to security incidents and helps companies strengthen their IT security.
Benefit from doIT's Cyber Security Experts' Know-how
Still at the beginning or concrete ideas already? We are here to help you!
If you have already found a specific topic in the area of cyber security, feel free to arrange an IT security deep dive with us, where we can go into more detail together. If you don't yet have a concrete idea of how to set up your IT security, we are also happy to give you some advice. Arrange your appointment now and protect your company from cyber attacks!